Today’s digital forensics teams face many challenges in a world filled with an overwhelming amount of data. From multiple office locations to massive employee pools and remote workers, AD Enterprise provides deep visibility into live data directly at the endpoint, helping you conduct faster, more targeted enterprise-wide post-breach, HR and compliance investigations in a single, robust solution. With AD Enterprise, you can respond quickly, remotely and covertly while maintaining chain of custody, and facilitate focused forensic investigations and post-breach analysis, without interruption to business operations.
AD Enterprise
Images
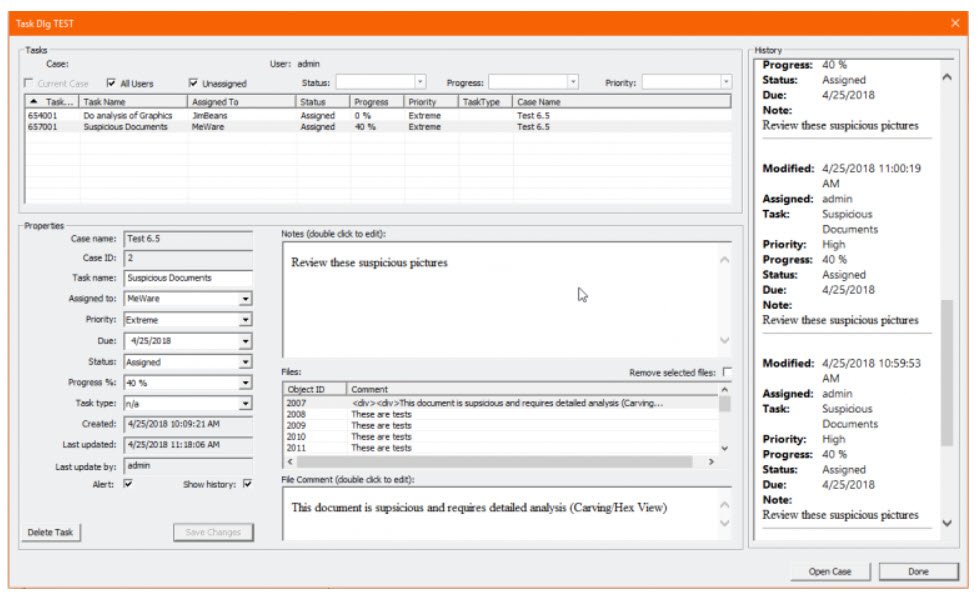
Check Software Images
Customer Reviews
AD Enterprise Reviews
User in Government Administration
Advanced user of AD EnterpriseWhat do you like best?
As a basic forensic tool,it is good and I have been using it for the past 11 years.
What do you dislike?
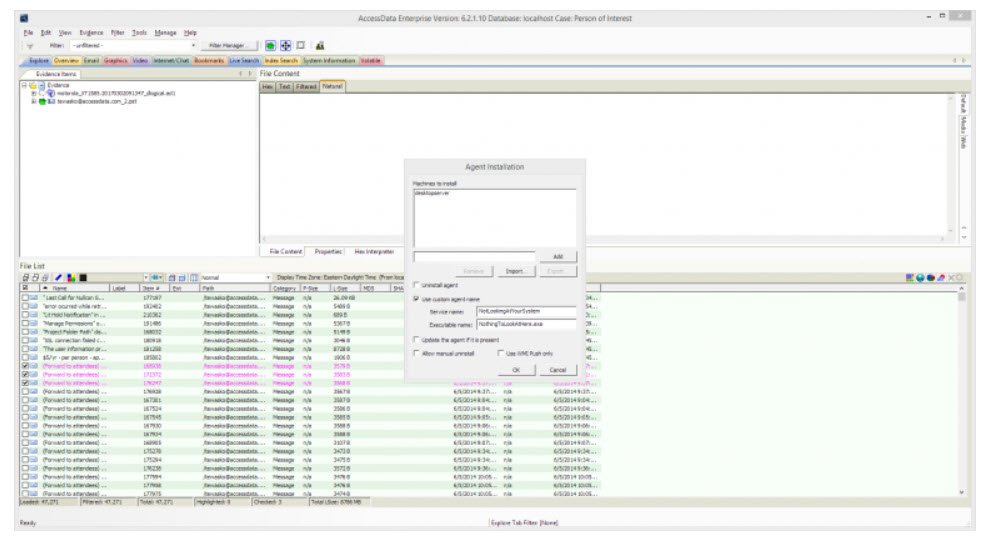
Where do I start? Remote acquisition is problematic. To start with certificate generation at installation was fraught with issues. There was no clear step-by-step to generate the correct certificates and it took many, many hours to work out what was actually needed. Self-generated certs, whic work straight away, are no good in an Enterprise environment. An error on the screen where certificates are selected still has not been fixed and was the cause of other issues as it suggests a certificate type that is incorrect.
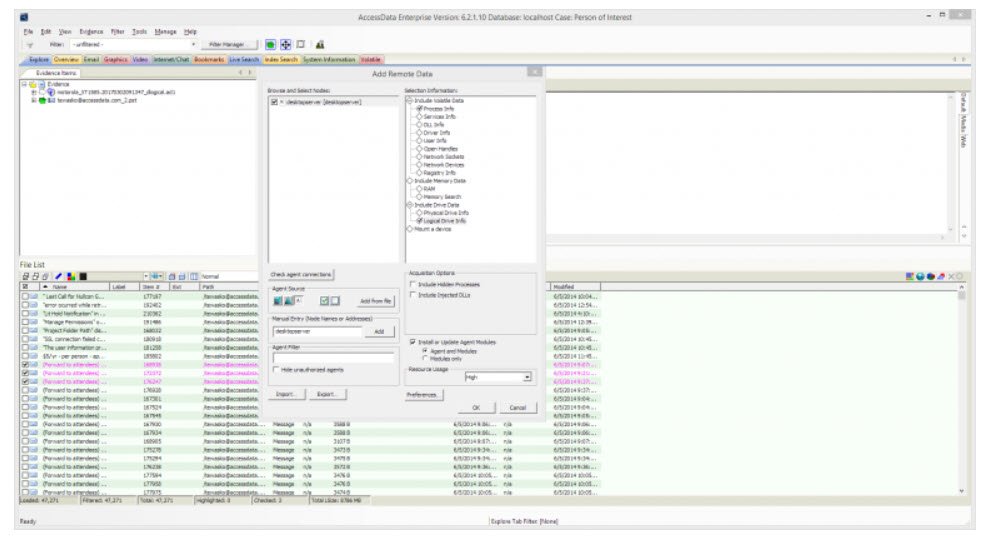
The other issue is that remote connections are far from straight forward. The system will not accept machine names and insists on only IP addresses and even then, connections 1st time are rare and usually requires several attempts and an agent re-install.
Our environment mandates that the system resides in a separate, secure Active Directory Domain and connections to the main Domain, where the target machines reside, makes it much more difficult. I have to launch FTK "as" the other Domain user in order to connect.
When agents run as a service and the connection is validated by certificate, there should be no need for further authentication as this complicates connections.
I just get the feeling that the this part of the system was designed by people with no forensic or system engineering background - clearly they don't appreciate just how difficult this part of the application is to use day-to-day.
There are other issues as well - too involved to mention here.
If I were to rate the remote-access portion out of 10 it would only get a 1. It needs a redesign - plain and simple.
I would also like to see a comprehensive user manual with real-world functional examples and explanations of features. It would be a big manual, but I really don't get the best out of its capabilities because I probably don't realise all its potential. For the money we paid for this system, the very least I expected was a straight forward installation and a comprehensive user manual!
What problems are you solving with the product? What benefits have you realized?
As described above, we don't use FTK to its full potential, however we have used it to uncover intrusions on some of our servers.