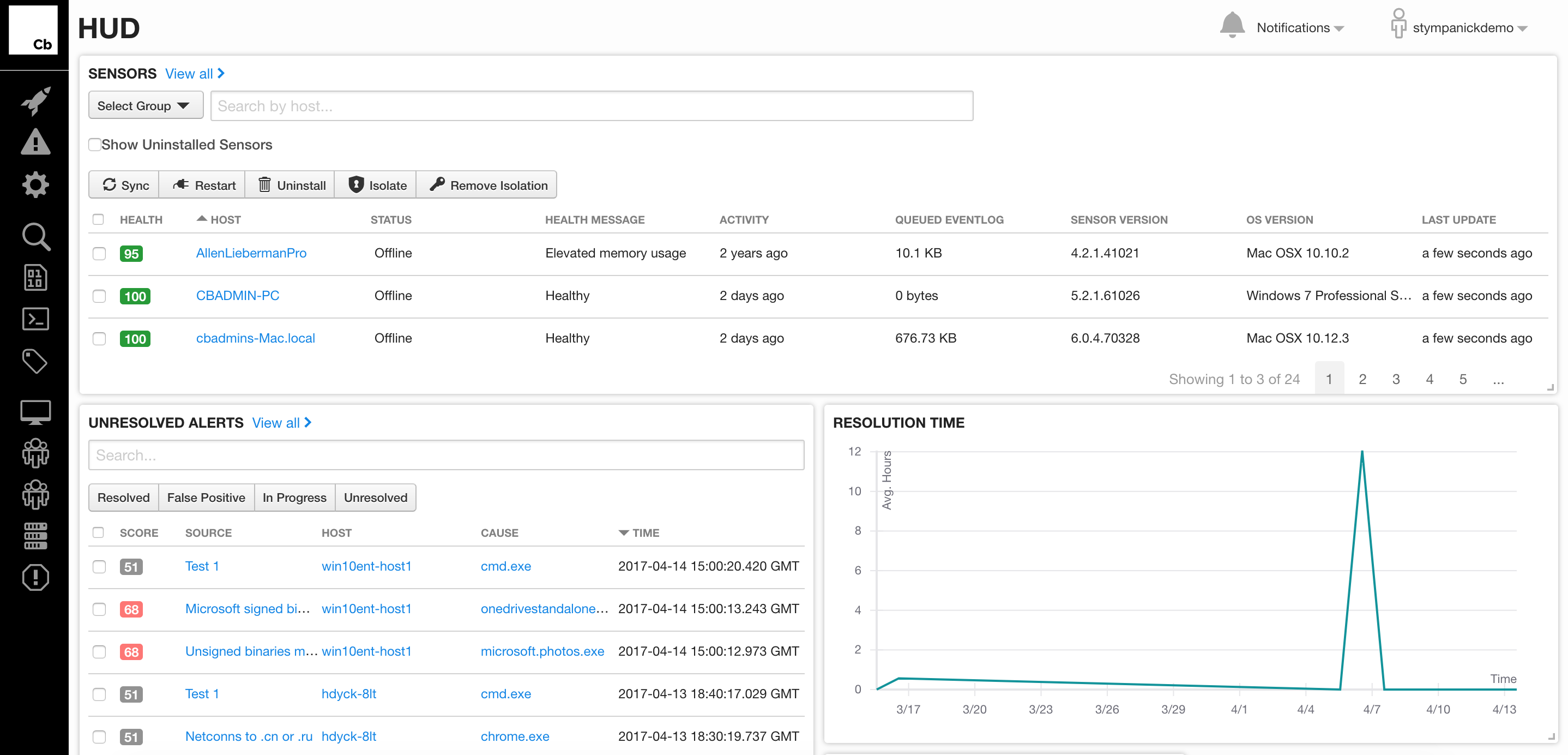
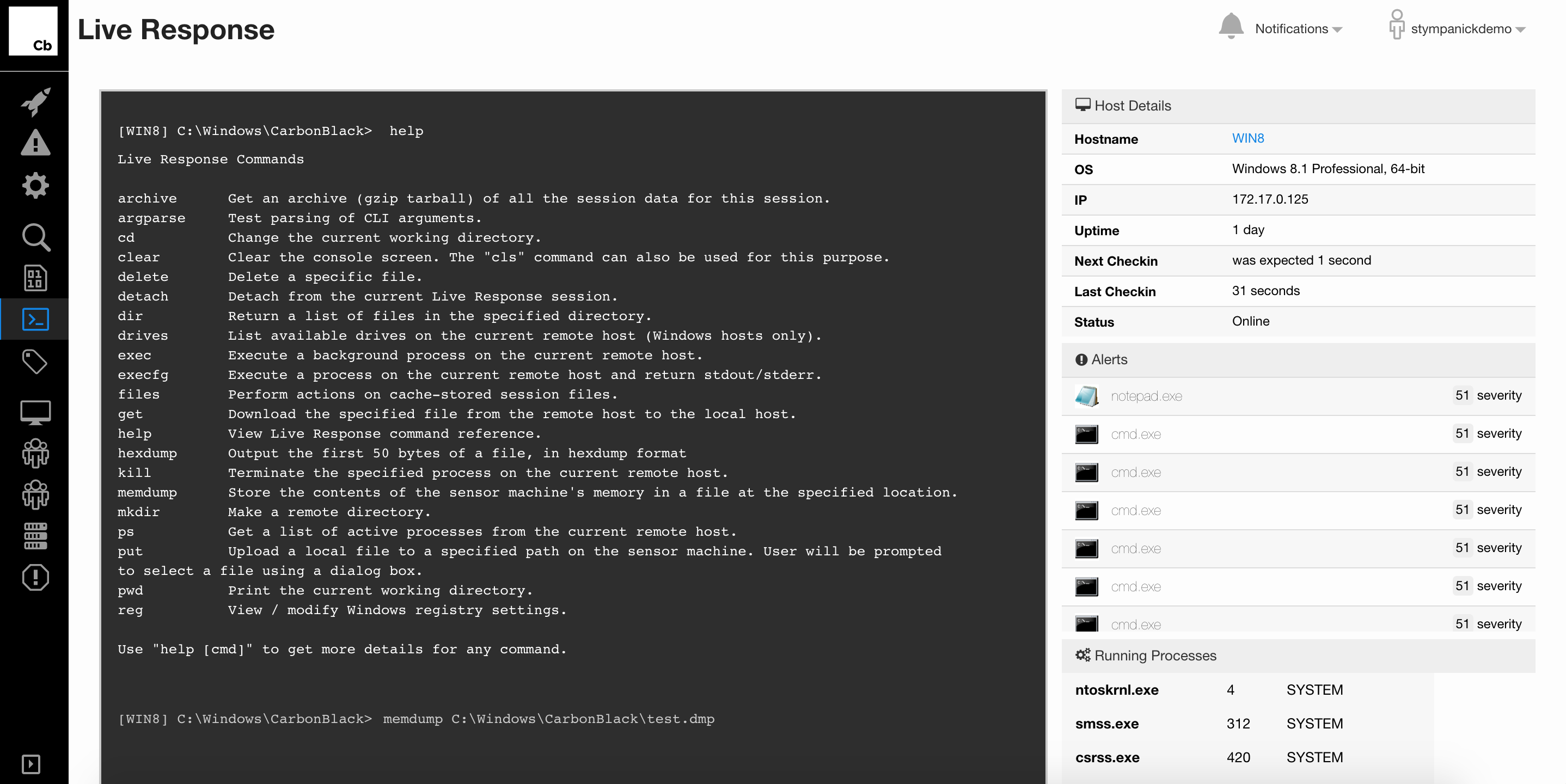
CB Response is the market-leading incident response and threat hunting solution designed to provide responders with the most information possible, accompanied by expert threat analysis and armed with real-time response capabilities to stop attacks, minimize damage and close security gaps. CB Response makes these teams more efficient, reducing investigations from days to hours, and more effective, enabling them to discover threats before attacks can exploit them. CB Response also allows teams to connect to and isolate infected machines to prevent lateral movement and remediate devices without costly IT involvement.
VMware Carbon Black EDR
Images
Check Software Images
Customer Reviews
VMware Carbon Black EDR Reviews
Swapnil R.
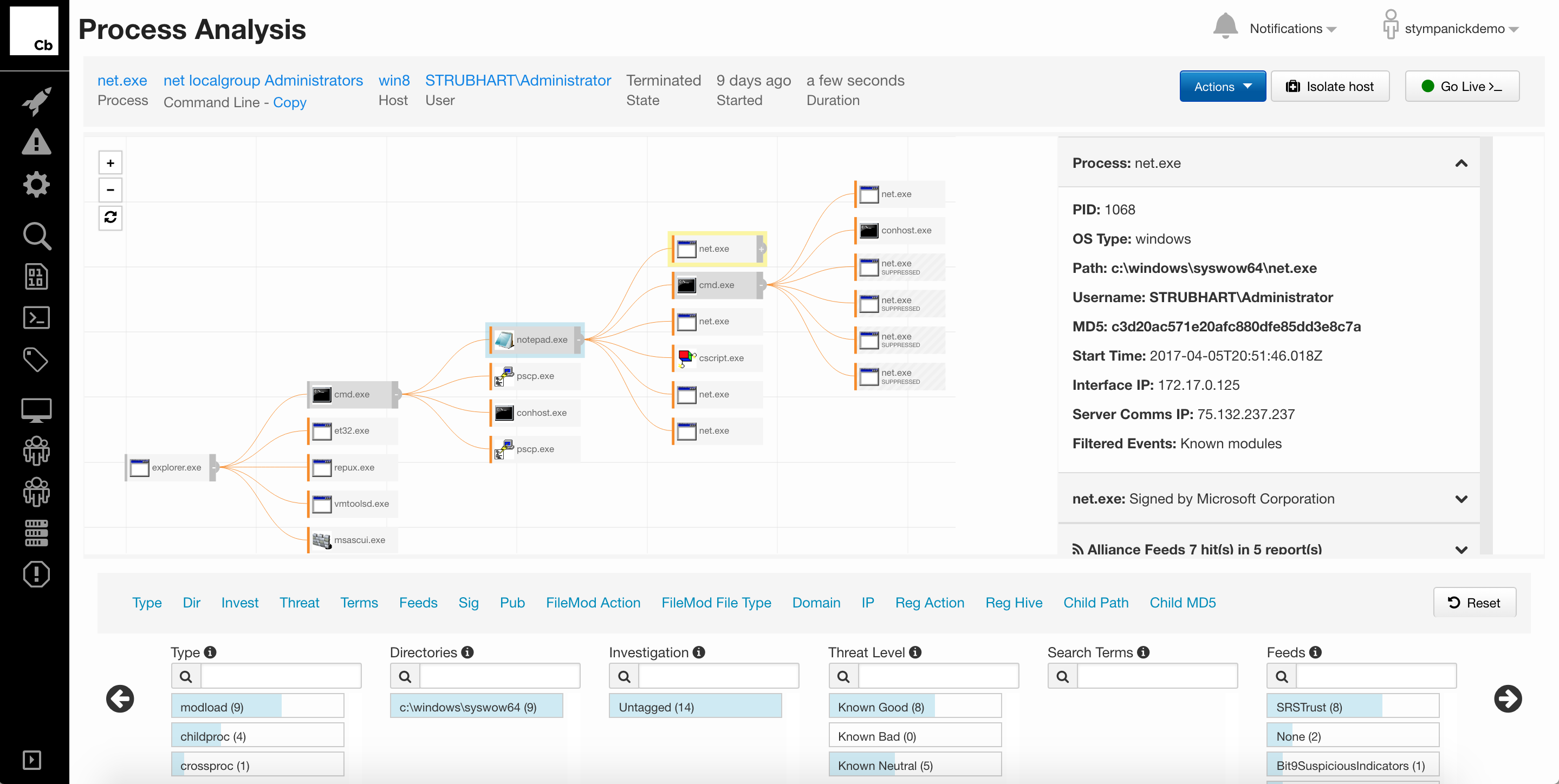
Advanced user of VMware Carbon Black EDRWhat do you like best?
When securing the enterprise organizations we cannot only depend on SIEM, threat intelligence and firewall management. Protecting internal endpoint devices is one of challenging job for the organization. Carbon Black Response defend against known as well as emerging threats, so the endpoint users work with confidence that their devices are secured. It is user friendly and very effective tool when we consider the endpoint security and Threat hunting. It gives complete visibility of every endpoint/sensors in organization. It provides threat intelligence feeds and reports for all know threats and malware signatures. It also provides customization watchlists by creating own queries so we can set alerts according to requirement. Process and binary searches are very good feature and very useful for threat hunting. We can block/ban the binaries and also isolate the endpoint which is best of the tool.
What do you dislike?
Analyst requires good skills for investigate and threat hunting purpose, it is somewhat difficult for beginners to work on CB Response as it requires deep knowledge of all the processes and it's executions.
Threat Intel reports generate some false positive alerts which are hectic sometimes.
Recommendations to others considering the product:
CB Response is must have tool for all security professionals. It is very helpful for effective threat hunting and securing the endpoints. It gives complete visibility of each and every process executing on the endpoint devices.
What problems are you solving with the product? What benefits have you realized?
Benefits are you can do threat hunting very effectively by deeply hunting IOC's and threat signatures. Problems we facing that we have to manually check the reputations of the binaries. It is better if tool give reputations or can give functionality to call API of some reputation check sites.