UTMStack is an All-In-One Unified Threat Management Platform that aims to simplify Cybersecurity and reduce its cost.
We are a small company focused on software development. Our headquarters are located in Florida, USA. Visit our website for more information about us: https://utmstack.com
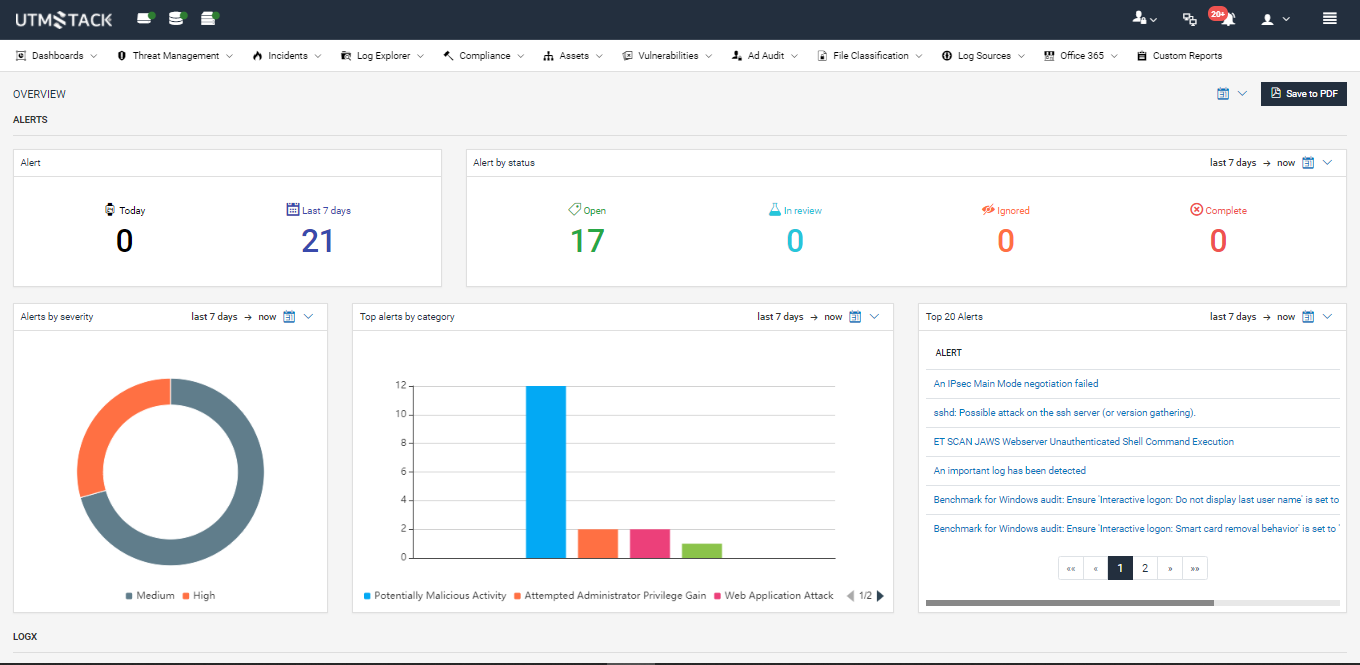
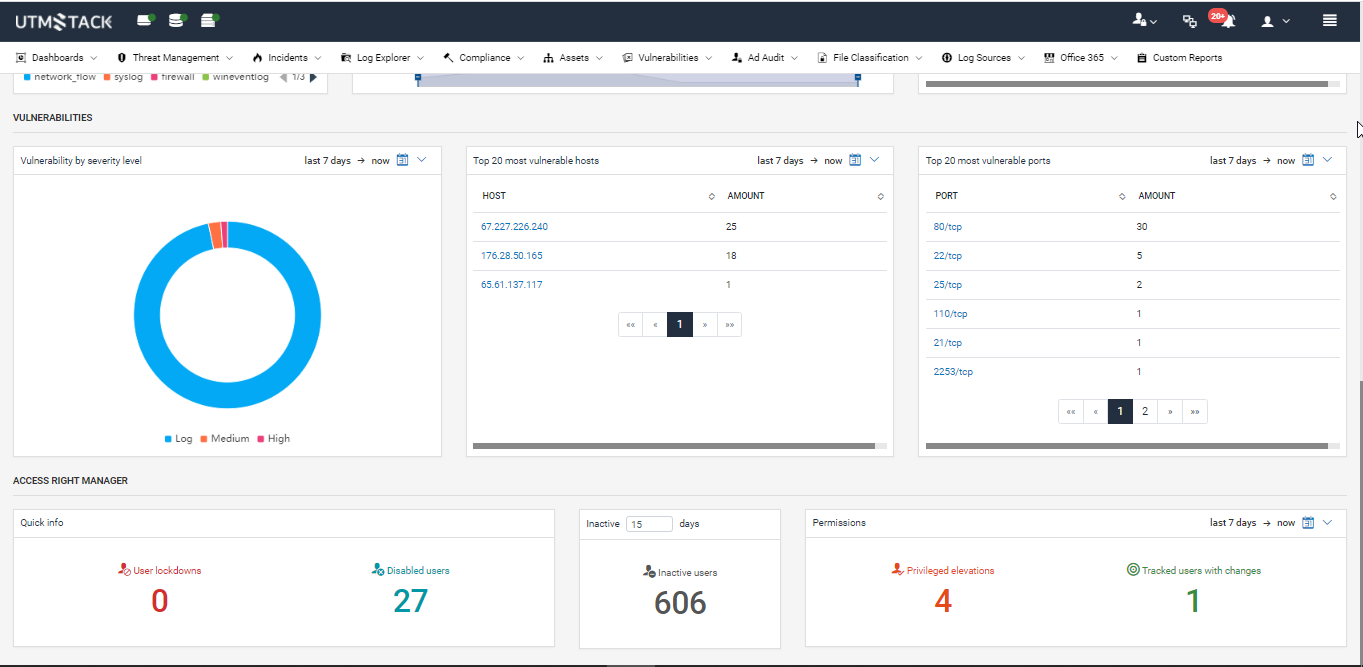
UTMStack provides complete visibility over the entire organization from a centralized management dashboard.
All solutions in the stack are fully integrated with each other and report to a central database. UTMStack features:
1. Log Management (SIEM)
2. Vulnerability Management
3. Access Rights Auditor
4. Incident Response
5. HIPS/NIPS, Endpoint Protection
6. Dark Web Monitoring
You can monitor almost any cloud environment or SaaS application with ready to use Integrations. UTMStack is currently integrated with Azure, AWS, Google Cloud and Integrated with SaaS and PaaS such as Office365 and AWS Lamda.
The UTMStack cybersecurity platform is made of multiple proprietary and Opensource pieces of software that, address different aspects of security and compliance.
They combine into a centralized correlation and classification engine powered by AI to provide threat detection and incident response capabilities.