What do you like best?
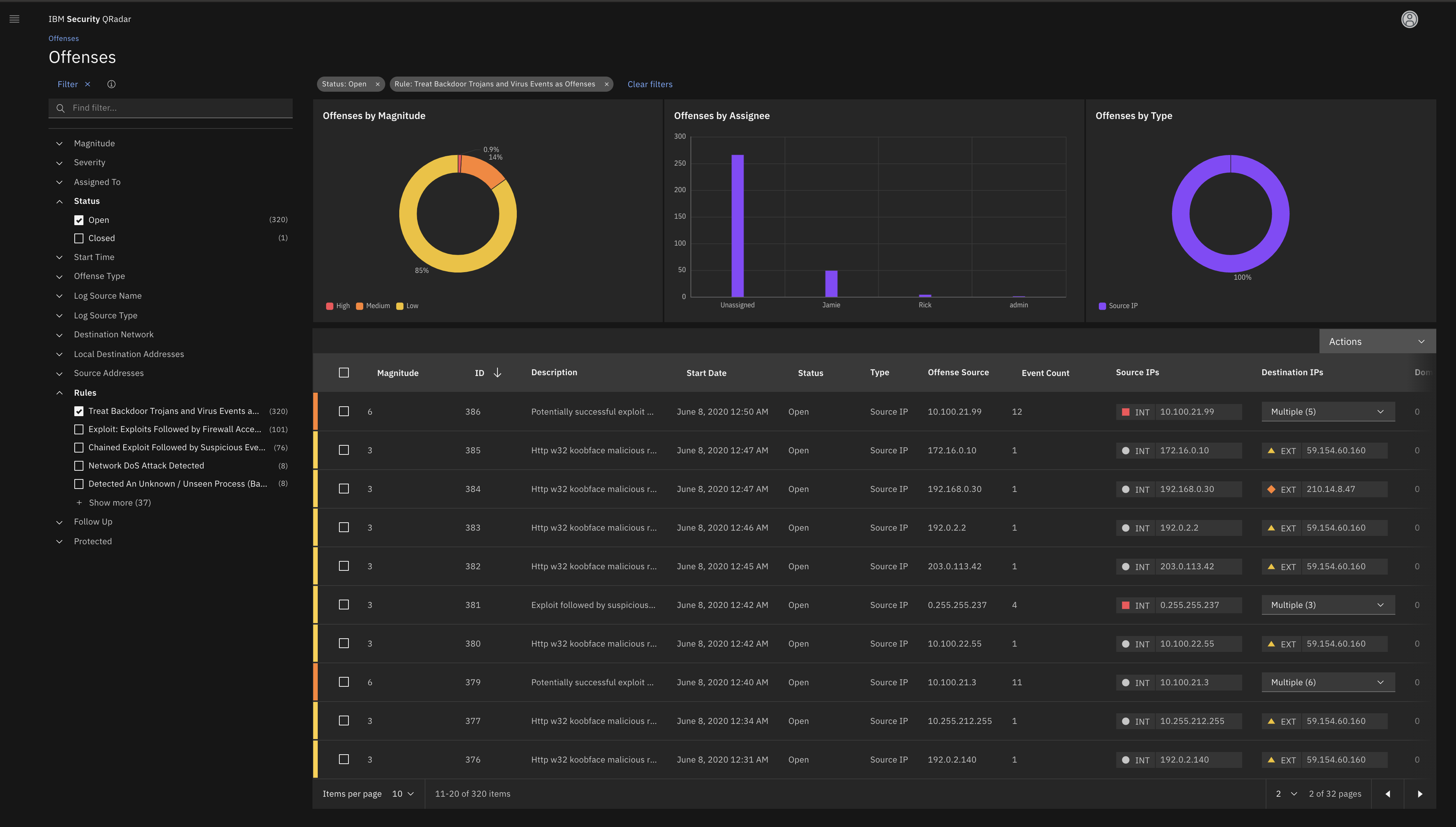
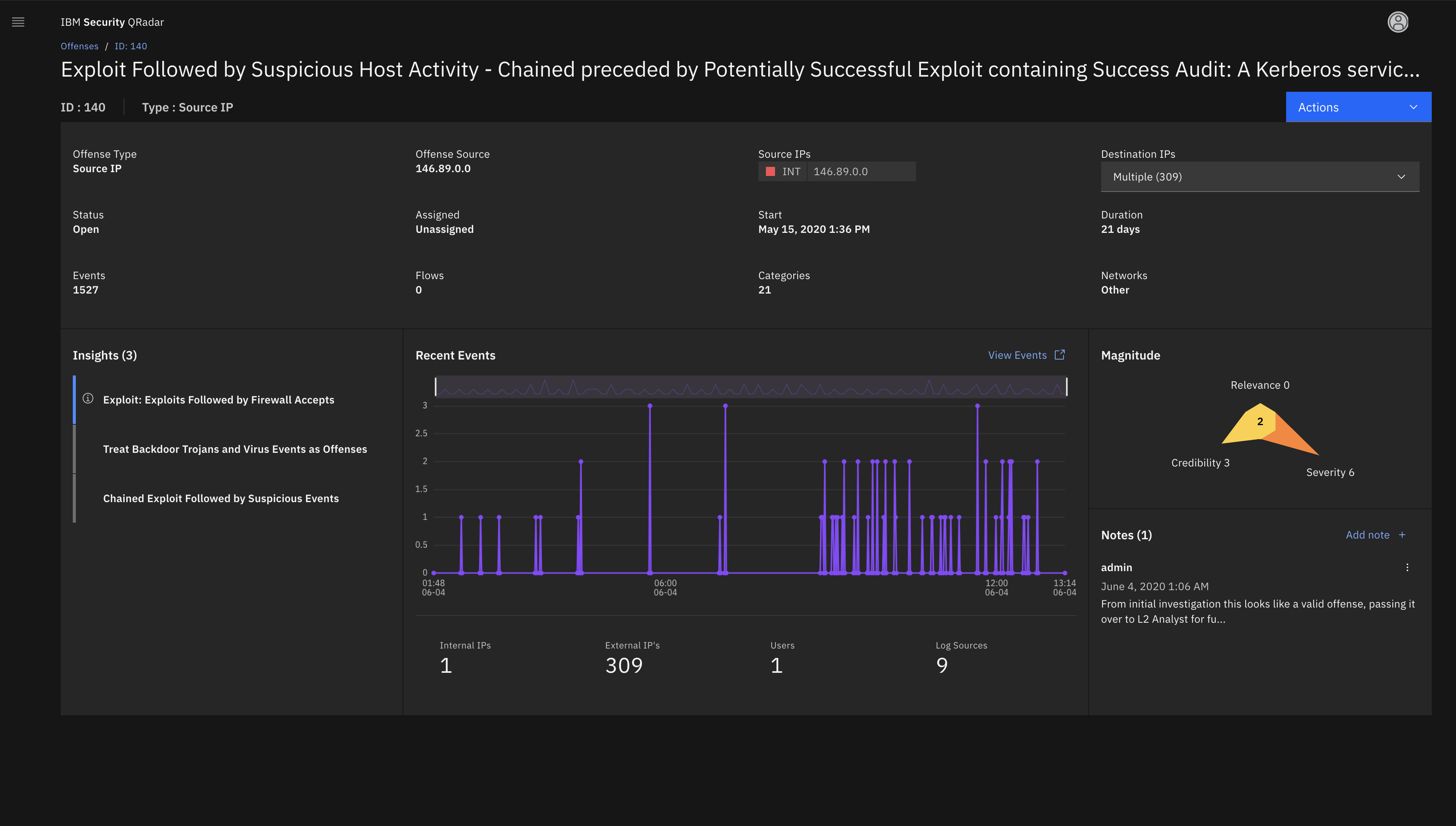
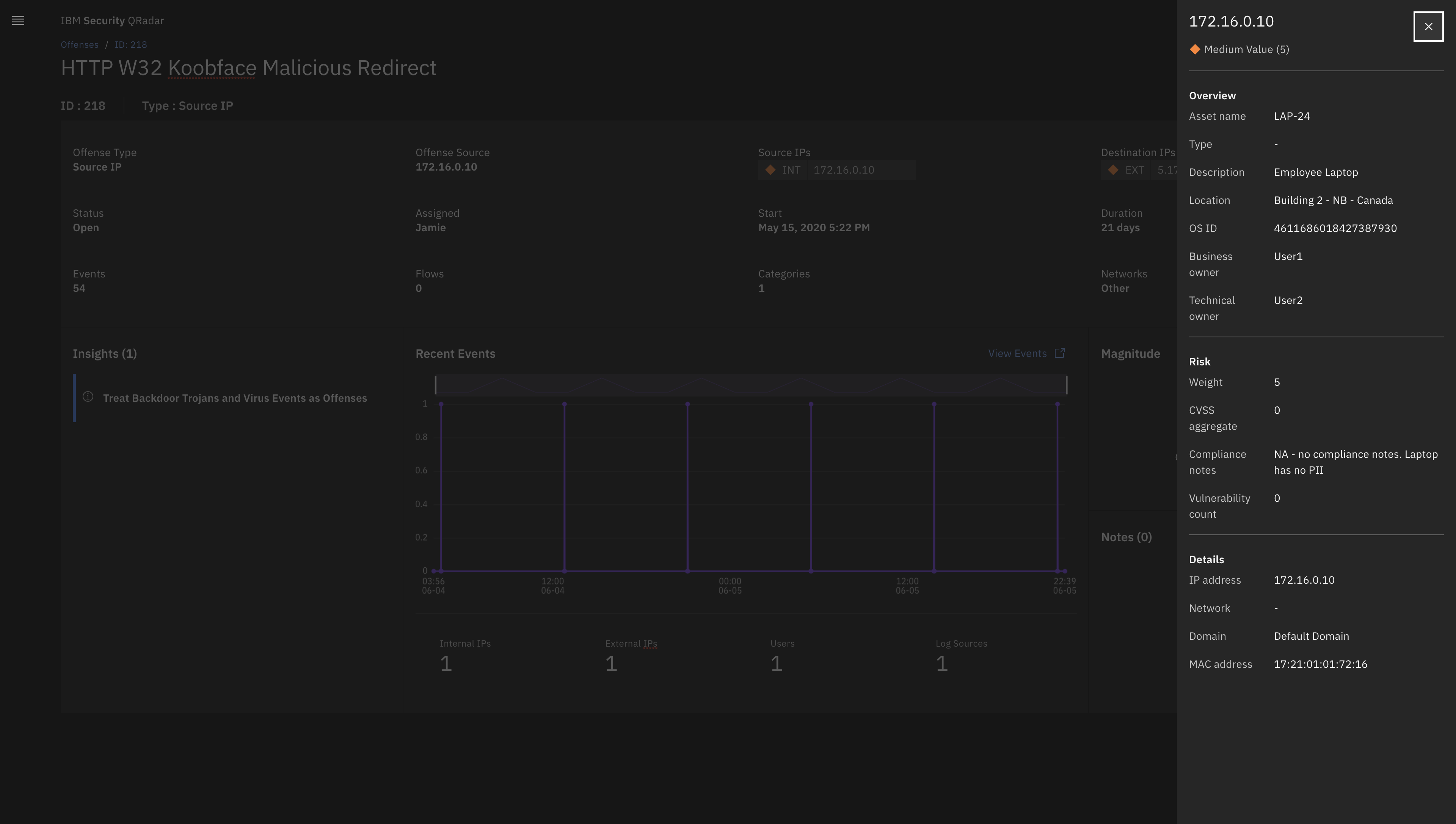
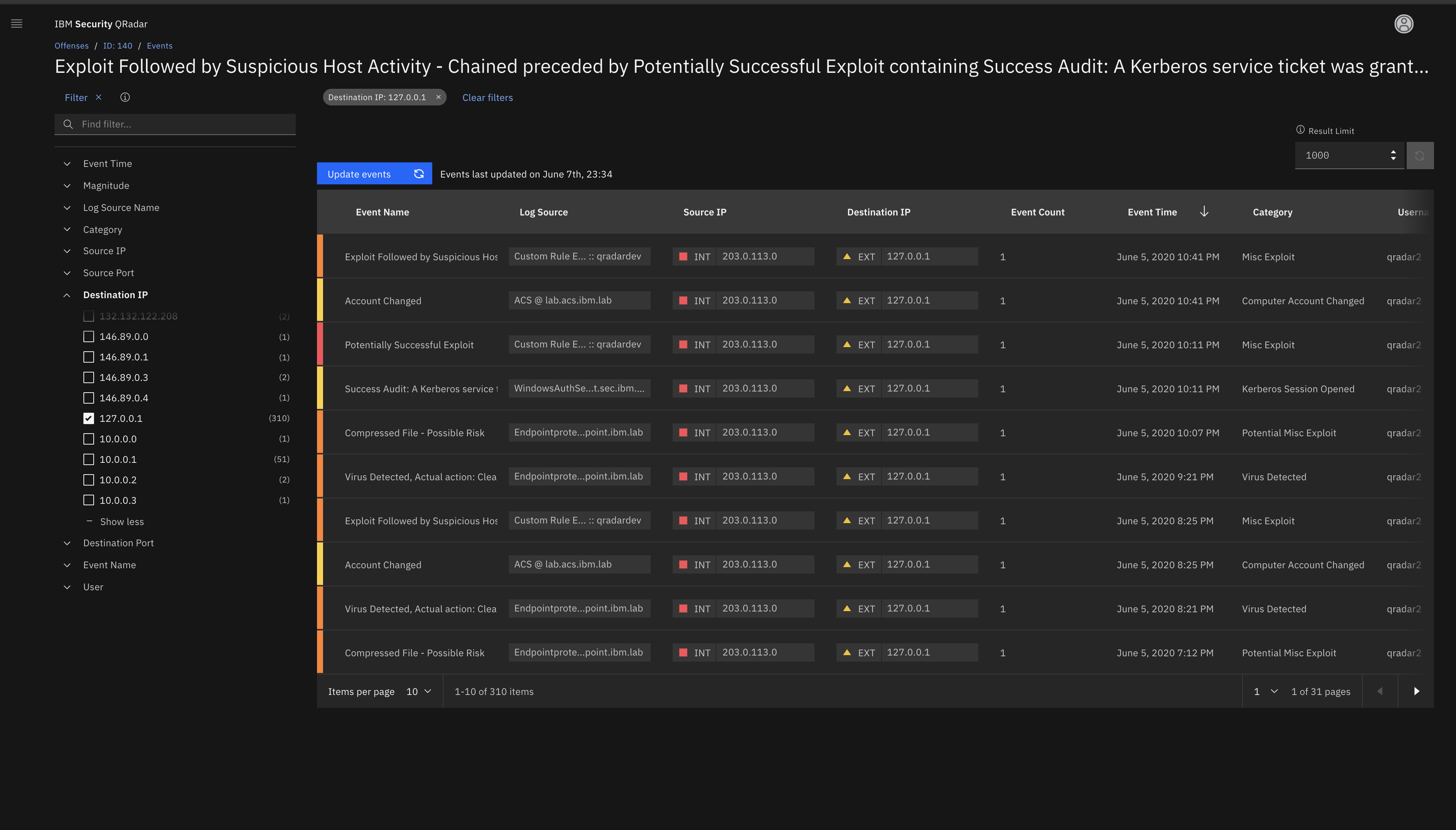
It is a very complete tool that includes the Zero Trust cybersecurity model, in addition to being incorporated with many products on the market as well as its easy handling and the components that can be incorporated. This tool has a high level of analysis of the offenses with the use of X-Force and Watson, also the generation of the graphical relationships of these offenses are very structured and allow a greater vision of each event.
What do you dislike?
Nothing so far the tool is excellent and meets all requirements.
Recommendations to others considering the product:
It is an excellent tool that has many elements that complement the management of security events. I recommend it for all types of organizations since it helps a lot with the management and monitoring of the entire infrastructure to prevent security incidents as well as to maintain an adequate level of risk and have a broader vision of the network infrastructure and services. .
What problems are you solving with the product? What benefits have you realized?
With the implementation of the solution, the adjustment of security policies has been drastically improved, as well as the monitoring and discarding of false positives in a faster and more efficient way. It has also helped us to monitor users and measure their level of risk, as well as vulnerability scans scheduled on specific dates to systems and network equipment to initiate mitigation plans for these vulnerabilities and to be able to correct them according to their level of criticality.