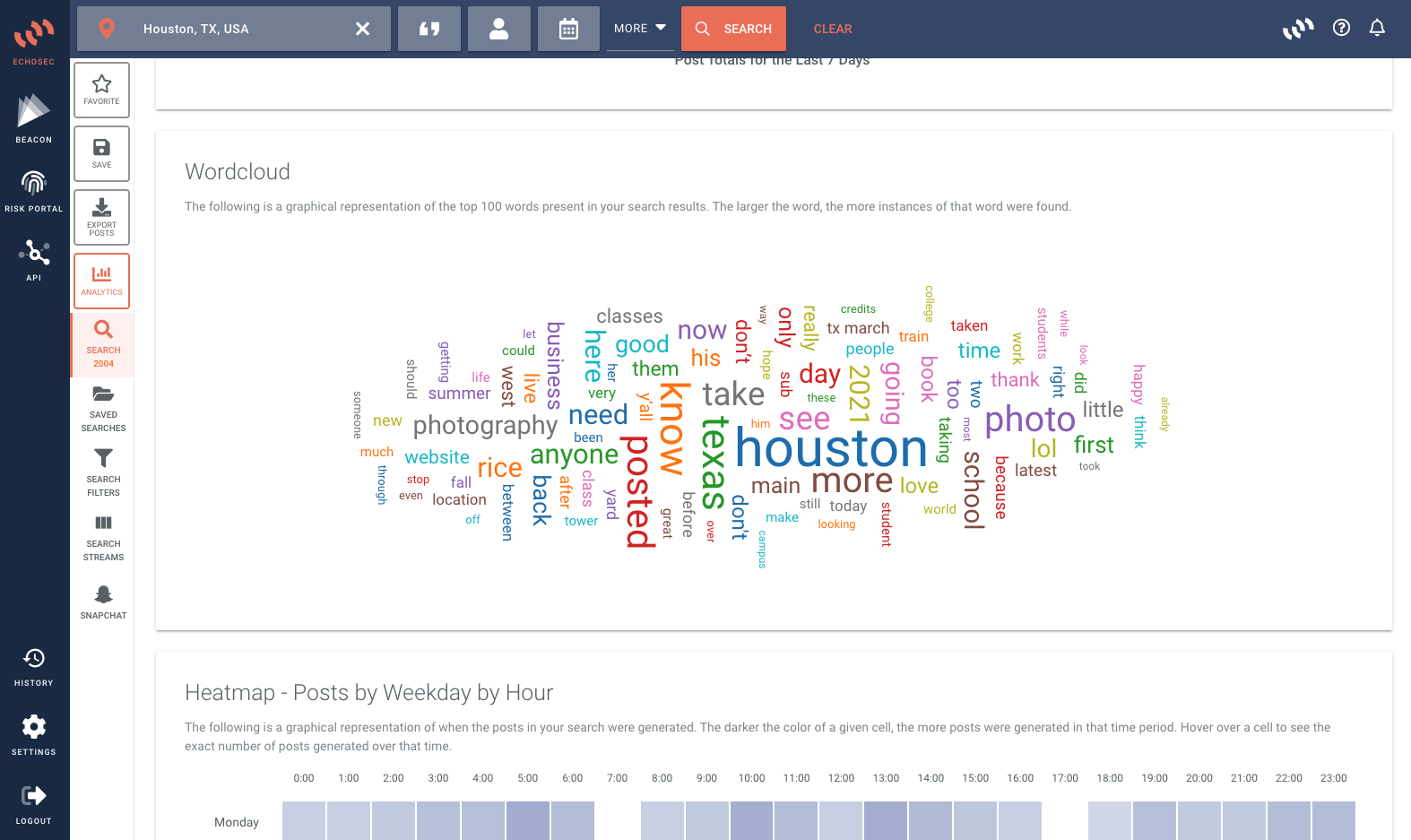
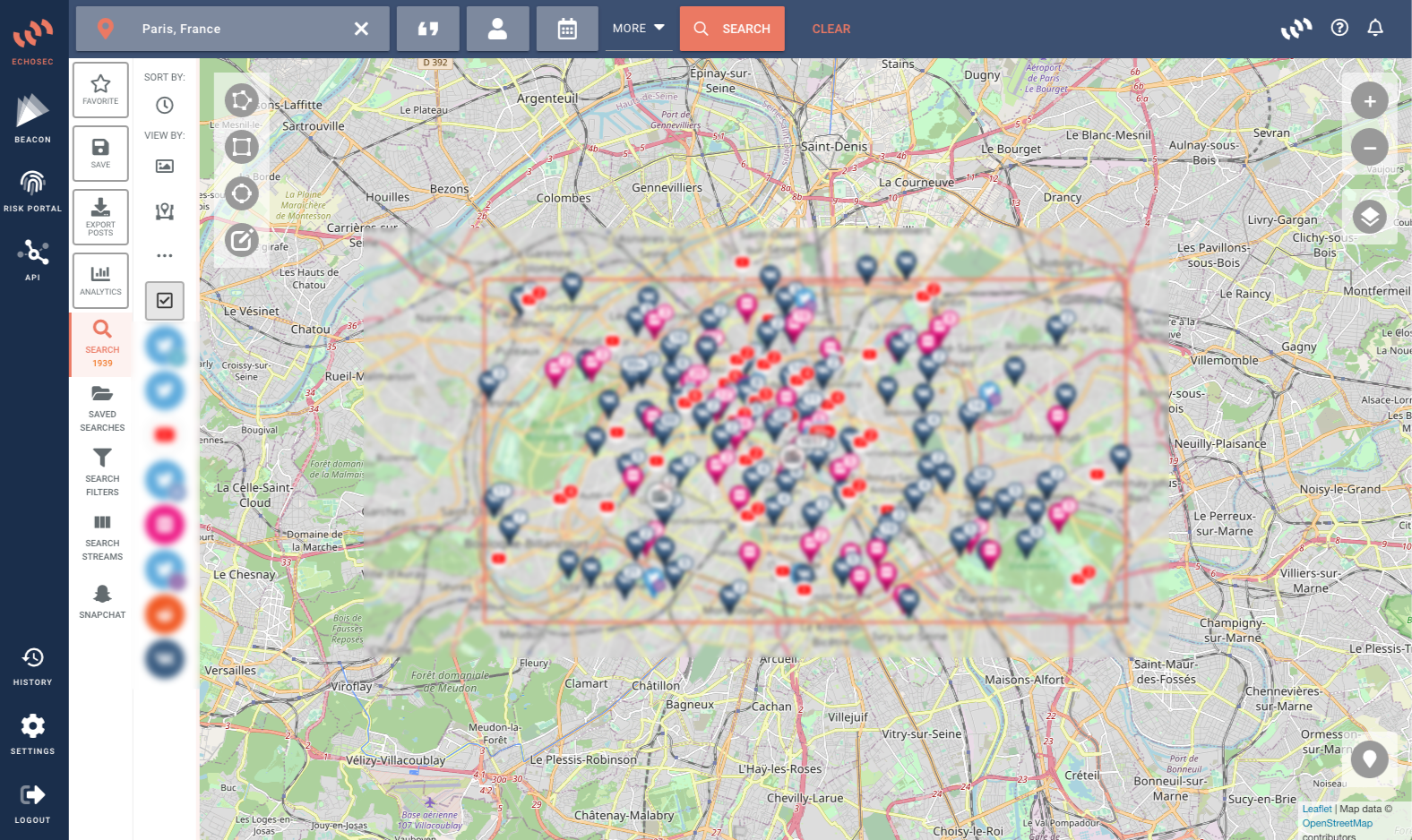
For security and intelligence teams, the internet is a valuable yet overwhelming source of data for threat intelligence.
Echosec Systems gives users a single point of access to a wealth of online data so they can respond faster and more effectively to cyber-enabled threats and real-world events. Our threat intelligence Platform delivers raw data from an unparalleled breadth of online sources in a simple user interface, allowing users to filter out irrelevant data quickly, for a more timely and informed response.
Whether the event is a violent threat, a planned attack, or a data breach—Echosec Systems offers 24/7 social media and dark web monitoring for immediate alerts and situational awareness.