Prey is a software and online platform for mobile device tracking, management, and data protection available for laptops, tablets, and mobiles. It offers a range of services for both personal and corporate use. The software and service are developed by the Chilean company Prey Inc., the successor of the funding company Fork Ltd.
The Prey service is the property of Prey Inc., a small software company that operates in Chile and San Francisco. To this day, Prey has over 7.000.000 users and protects more than 8.800.000 devices in over 230 countries around the world. The service can be accessed for free, with the basic protection plan, or in its paid alternative that adds extensive features. The latter offers data protection tools for personal users, and a device fleet management suite for enterprises, schools, and non-profit organizations.
рќ—Єрќ—›рќ—”рќ—§ рќ—–рќ—”рќ—Ў рќ—¬рќ—ўрќ—Ё рќ——рќ—ў рќ—Єрќ—њрќ—§рќ—› рќ—Јрќ—Ґрќ—рќ—¬?
– Advanced Tracking
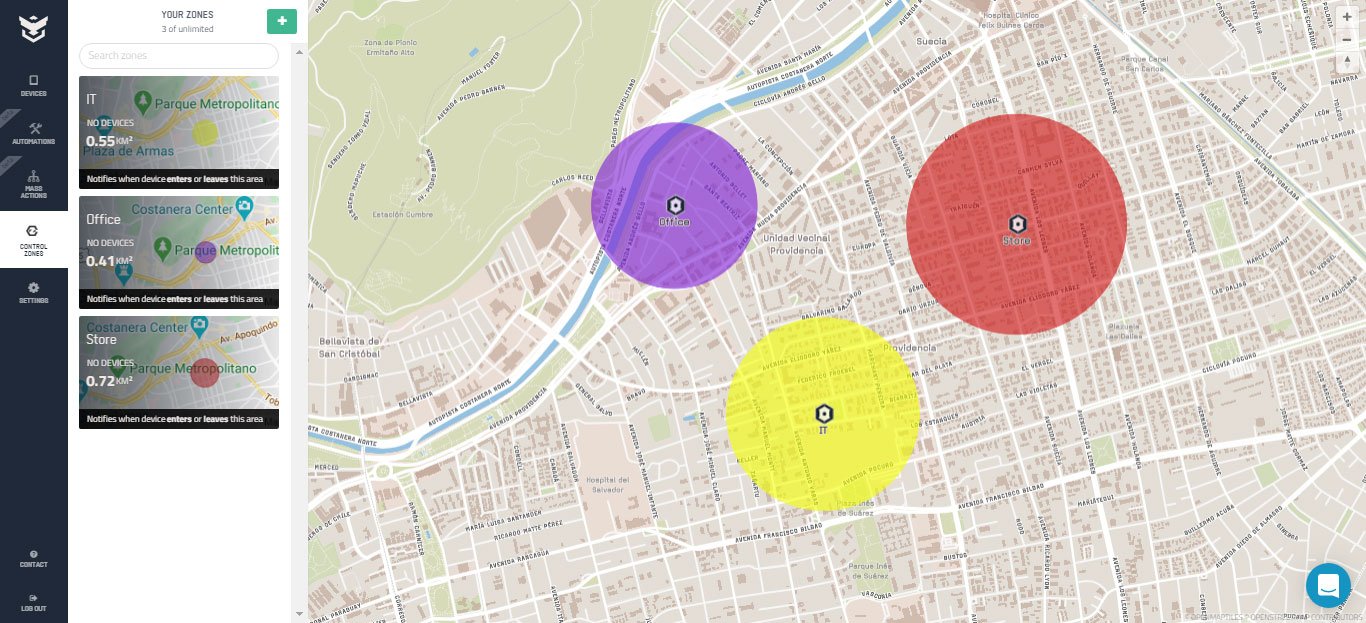
Follow a fleet’s movements globally, track their locations in time, and delimit Control Zones to detect and react to unwanted area exits or entries.
– Reactive Security:
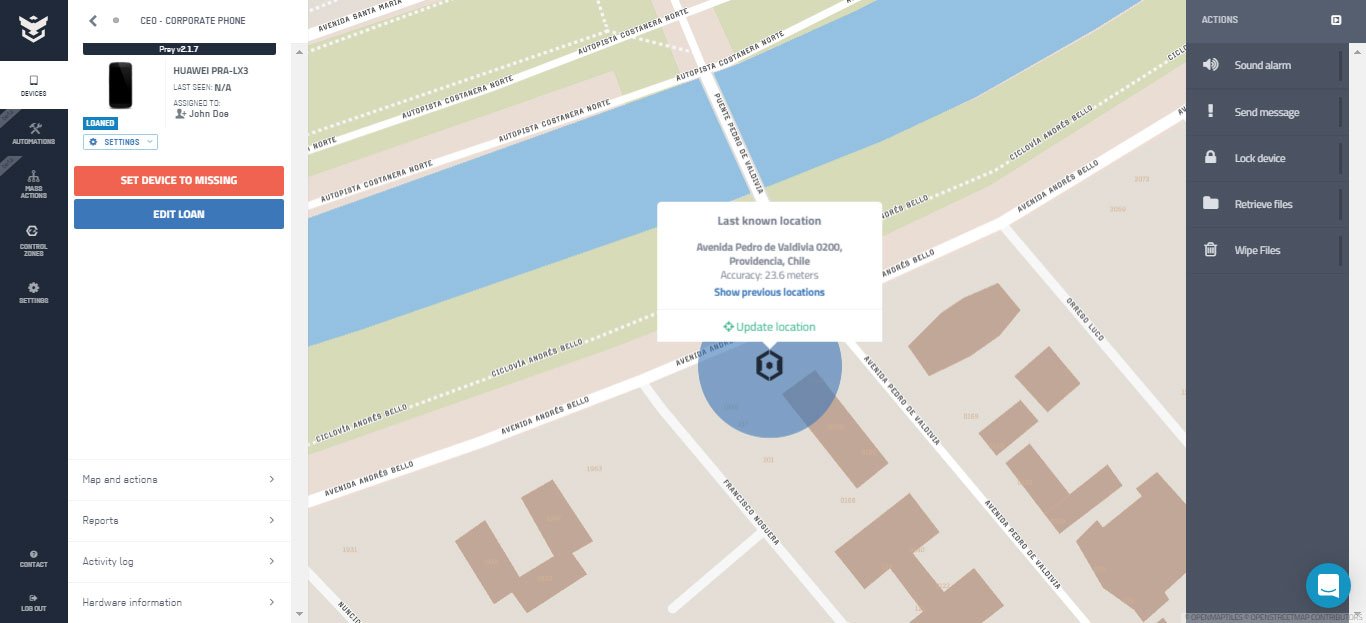
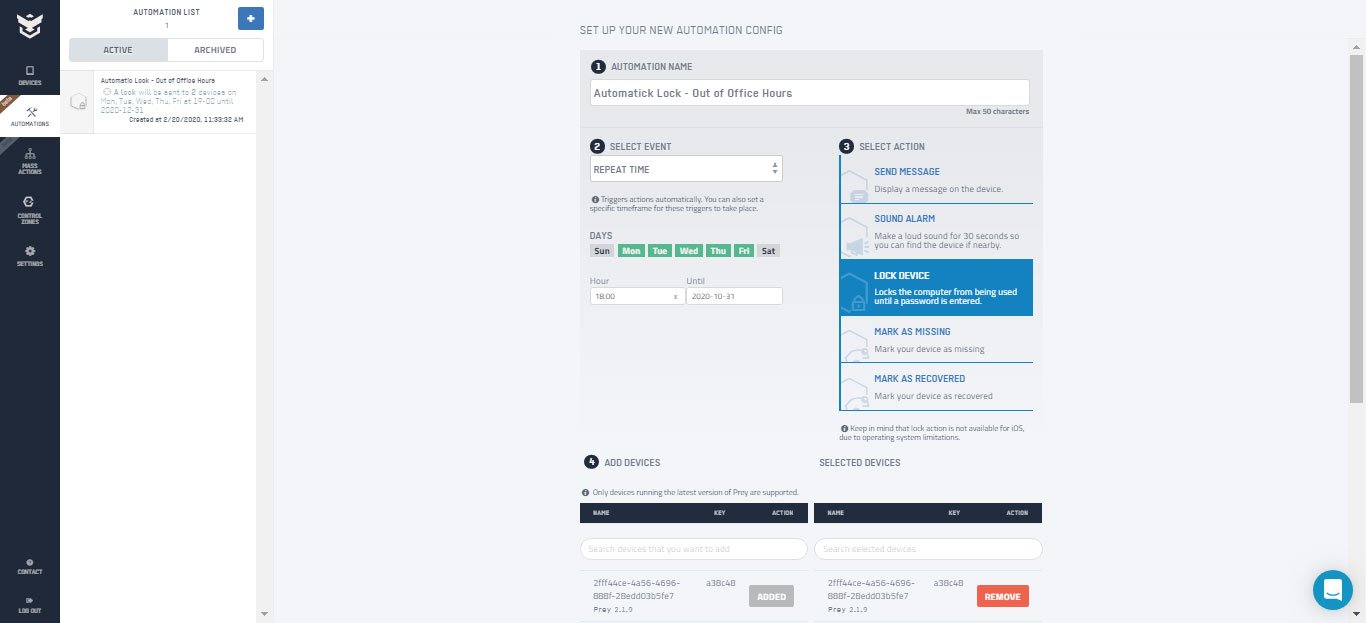
Create automatic triggers for when theft or movement is detected, and use anti-theft tools to block and track your organization’s assets. Recover key files, wipe or lock-down the rest, and gather evidence.
– Simplified Management:
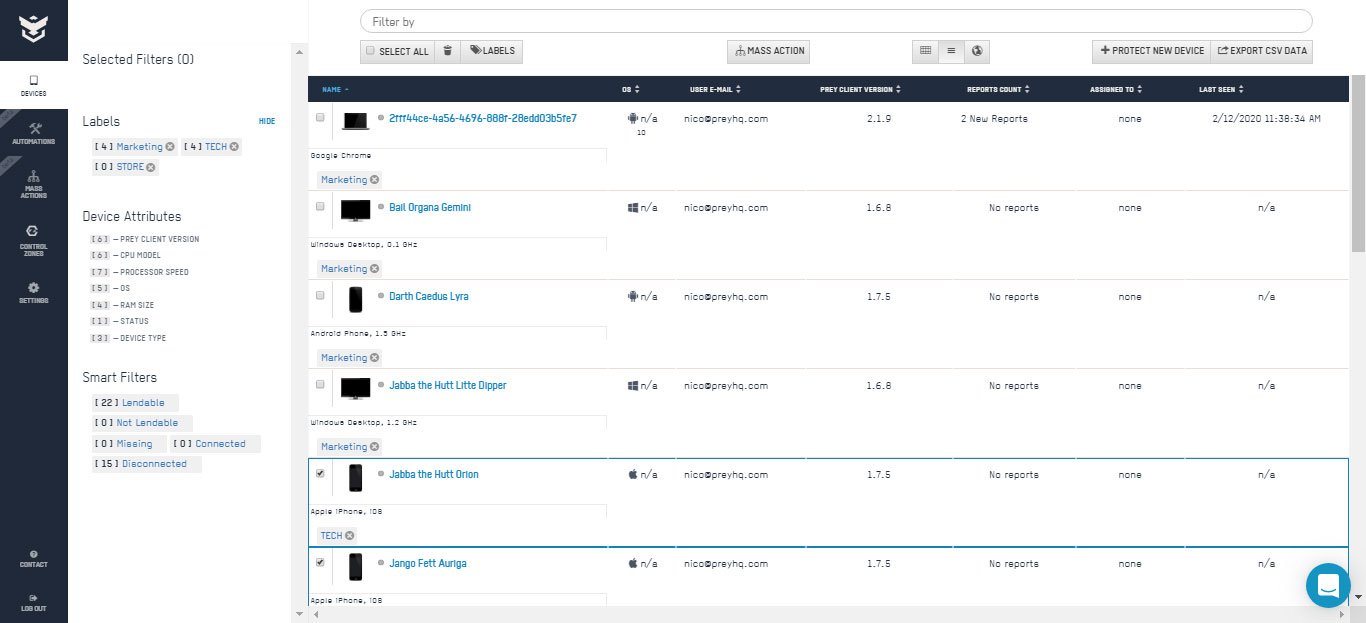
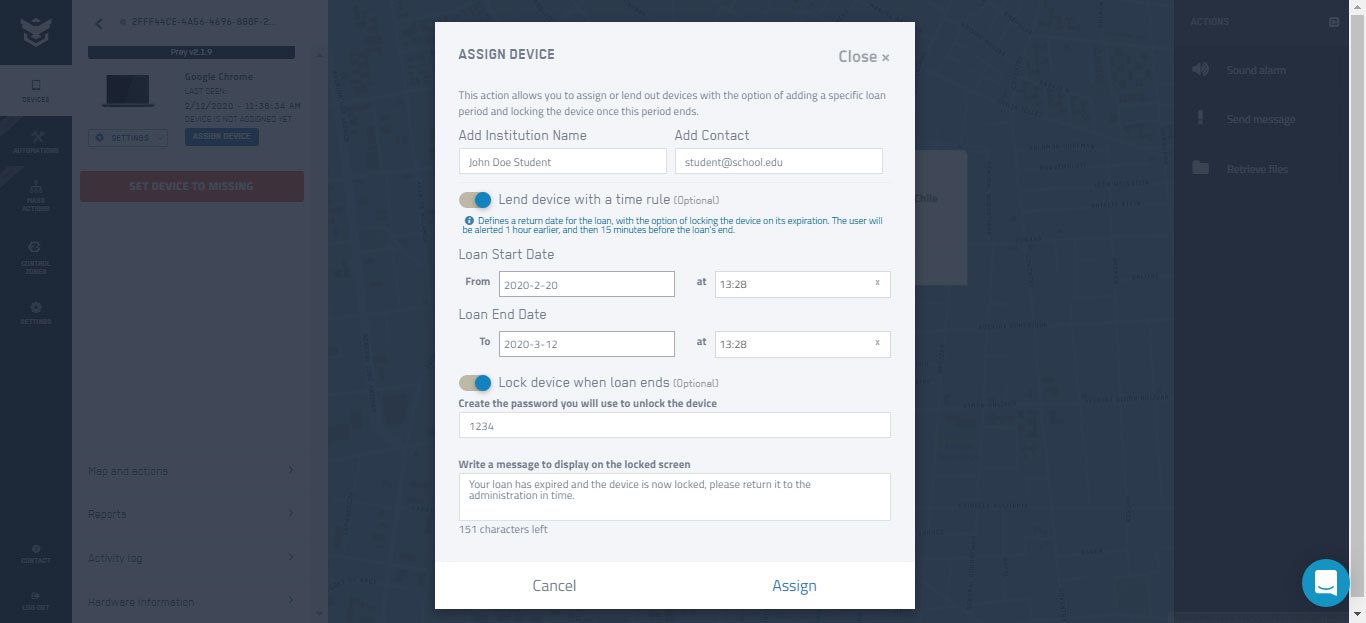
Assign devices to employees, easily group them by usage, hardware, or area, and keep track of any hardware changes or odd behaviors like devices that have been offline for a while.
– Evidence-based Recoveries:
When a device is missing, Prey will gather evidence that’s crucial for recovery, and deliver it to you in periodic reports that can aid the police’s work.
рќ—™рќ—рќ—”рќ—§рќ—Ёрќ—Ґрќ—рќ—¦ рќ—•рќ—¬ рќ—–рќ—”рќ—§рќ—рќ—љрќ—ўрќ—Ґрќ—¬.
TRACKING AND LOCATION
– GPS, Wifi Triangulation, and GeoIP Tracking
– Control Zones (Geofencing)
– Global Device View
– Location History
DEVICE SECURITY
– Remote Screen Lock
– Message Alert
– Anti-mute Alarm
– Control Zone Actions (Movement-triggered actions)
DATA SECURITY
– Remote Wipe
– File Retrieval
Device Management
– Scheduled Automations
– Mass Actions
– Enterprise Inventory
– Custom Labels and Search
– Fleet Status Dashboard
– Custom Deployments
MISSING EVIDENCE REPORTS
– Pictures and Screenshots
– Active and Nearby WiFis
– Coordinates and Map
– Device Information
– Mac Address and IP
рќ—Єрќ—›рќ—¬ рќ—–рќ—ўрќ— рќ—Јрќ—”рќ—Ўрќ—њрќ—рќ—¦ рќ—–рќ—›рќ—ўрќ—ўрќ—¦рќ— рќ—Јрќ—Ґрќ—рќ—¬
вњ” It unifies and monitors your whole fleet seamlessly.
Organize your laptops, tablets, and mobiles in groups and follow their status and position globally. Control Zones will help detect unwanted movements that can be reviewed in time.
вњ” It adds an extra layer of data privacy compliance.
Make sure your fleet is ready to protect its data safety compliance against incidents that may put legally bound private data at risk using the platform’s custom wipe and file retrieval tools.
вњ” It reacts automatically and gathers evidence.
Configure automatic reactions upon movement detection to deter theft, and gather evidence to identify the thief. Or set up timed actions, like curfew locks to avoid usage out of office hours.