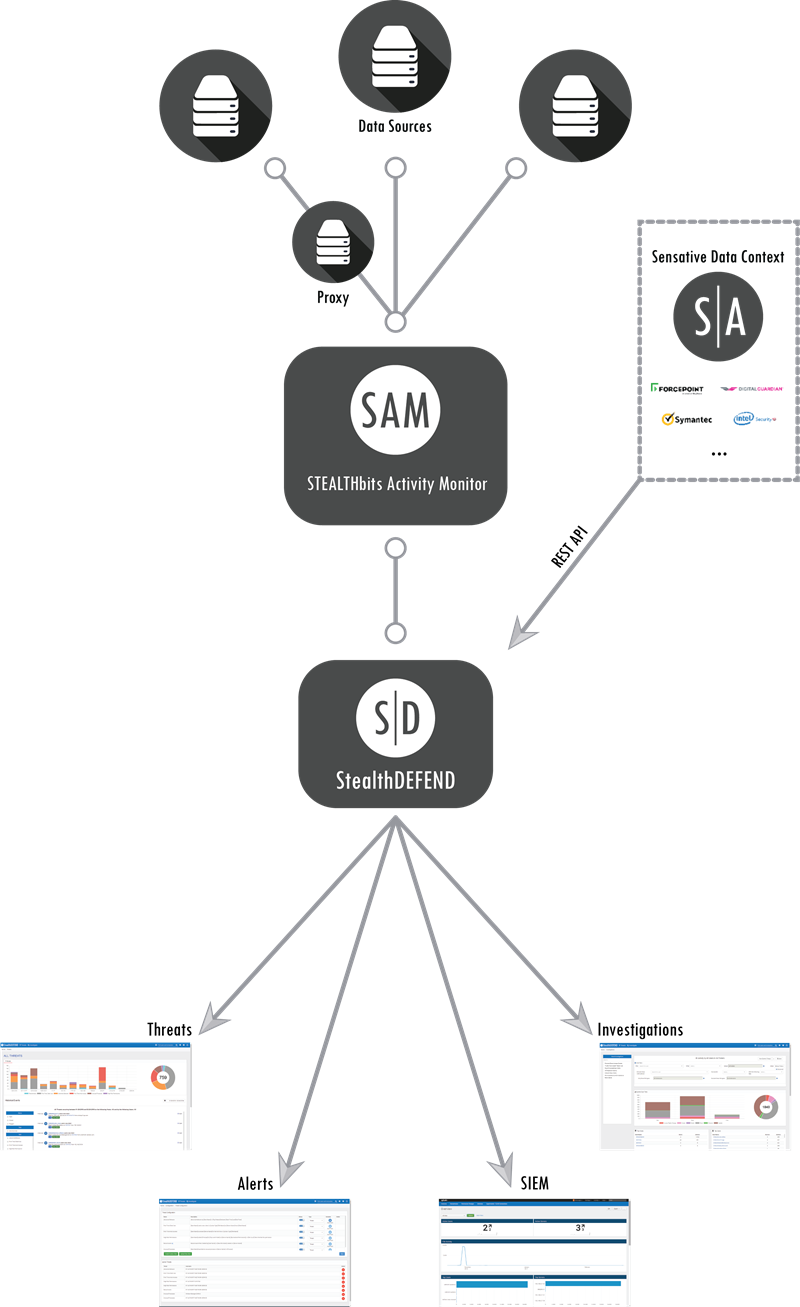
StealthDEFEND is the real-time threat analytics component of STEALTHbits’ Data Access Governance Suite. Leveraging unsupervised Machine Learning, StealthDEFEND eliminates excessive and undifferentiated warnings to surface truly meaningful trends and alerts on attempts to compromise your sensitive data.
TOP FEATURES:
– Unsupervised Machine Learning – Analyze a rich set of data with Machine Learning models that evaluate, correlate, and baseline the activity and behavior of users.
– Seamless Sensitive Data Integration – Threat and Data Access Governance information is seamlessly integrated, further reducing noise by honing in specifically on the files that matter most.
– Preconfigured Threat Models – StealthDEFEND has been purpose-built to detect file system threats associated with Ransomware, Abnormal Behavior, First Time Host Access, First Time Client Use, Unusual Processes, and more.
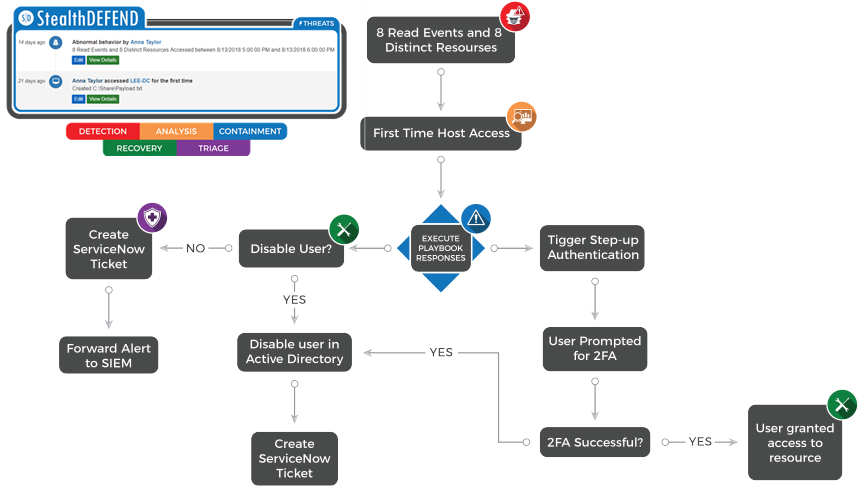
– Response Playbooks – StealthDEFEND’s actions engine automates security responses and connects various security applications and processes together with multi-stage actions. Out-of-the-Box or custom “Playbooks” can be leveraged to respond to threats automatically or programatically.
– User Behavioral Profiles – Concrete understanding of each individual user’s behavior is incorporated into StealthDEFEND’s threat analytics and Machine Learning models, complemented by visuals that make understanding any user’s normal behavior a trivial task.
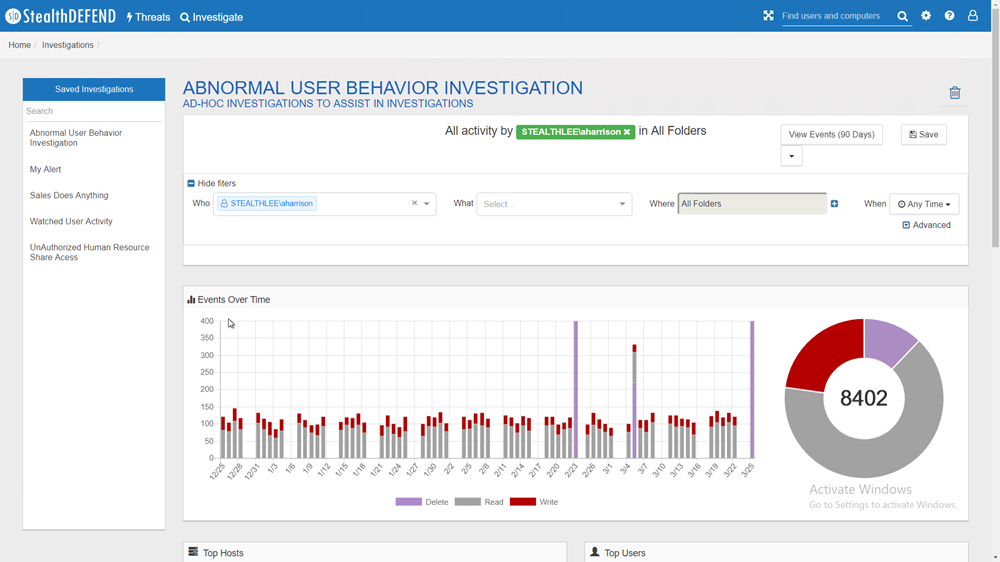
– Comprehensive Investigations – Create, configure, and save detailed reports, alerts, and threats on User and Group activity.
– SIEM Integration – Out-of-the-box SIEM integration and preconfigured dashboards extend ready-to-use functions.
– Real-Time Alerting – Real-time security alerts powered by Machine Learning allow you to master your threat data in a continuous way that leads to faster investigations and threat neutralizations.
– Interactive, Real-Time Visualizations – Through a unified web presentation layer, threat data is streamed, processed, and visualized as it happens, including modern visualization elements like heat maps that update themselves in real-time to bring data to life.
– Incident Detection Response Workflow – Quickly coordinate your team’s efforts so they’re prepared to share information and track who is working on an issue at any given time.